In a world where technology evolves faster than we can say “cybersecurity,” one might wonder if the Health Insurance Portability and Accountability Act of 1996 (HIPAA) is still relevant.
Surprisingly, it’s not just relevant; it’s an unsung guardian of our healthcare data.
Compliance with HIPAA is essential for healthcare organizations to maintain data security and protect patients’ sensitive health information. Non-compliance can result in severe penalties and legal consequences, so organizations must continuously assess and improve their security measures to meet HIPAA requirements.
To help ensure your healthcare organization is effectively navigating this government-mandated protocol, let’s explore the three areas of HIPAA security standards.
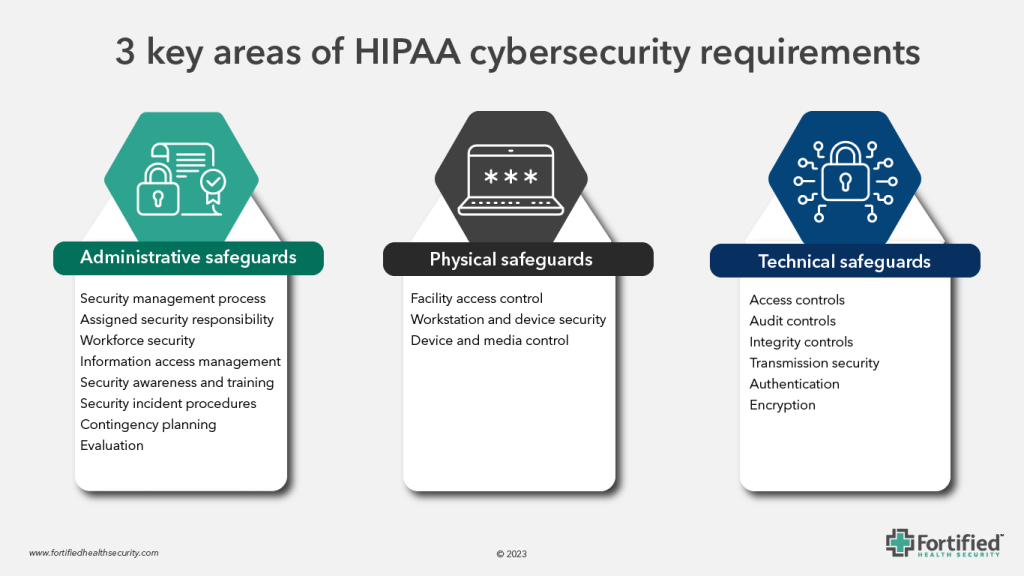
Administrative safeguards
Administrative safeguards refer to the policies, procedures, and practices that healthcare organizations put in place to protect the confidentiality, integrity, and availability of patient health information. They are a crucial compliance component of HIPAA and essential to a healthcare organization’s ability to foster a secure, trustworthy, and resilient healthcare environment.
There are eight administrative safeguards that hospitals and health systems need to fulfill to meet HIPAA cybersecurity standards:
1. Security management process
Covered entities (healthcare providers, health plans, healthcare clearinghouses, and business associates) are required to establish and implement security policies and procedures. This includes risk assessments to identify vulnerabilities, define security measures, and create an incident response plan.
2. Assigned security responsibility
Healthcare organizations should designate a security official responsible for developing and implementing security policies and procedures, as well as training and managing staff on security-related matters. This will aid in safeguarding patient data, maintaining compliance with regulations, managing risks, and maintaining the trust and reputation of the organization.
3. Workforce security
Entities are also charged with implementing policies and procedures to ensure that only authorized personnel have access to PHI. This includes training staff on security awareness and regularly reviewing and updating access privileges.
4. Information access management
Access to PHI should be controlled by establishing procedures for authorizing and revoking access, as well as defining the level of access that employees, contractors, and business associates have based on their roles.
5. Security awareness and training
Provide ongoing security training and awareness programs for all employees to ensure they understand their responsibilities related to protecting PHI.
6. Security incident procedures
Develop and implement an incident response plan to address security breaches or unauthorized access to PHI, including reporting and mitigating security incidents.
7. Contingency planning
Create data backup and recovery plans to ensure the availability of PHI during and after emergencies or disasters. This includes regularly testing and revising these plans.
8. Evaluation
Periodically assess the effectiveness of security measures, policies, and procedures through audits, evaluations, and reviews.
Physical safeguards
In the healthcare industry, a cyberattack isn’t always the biggest threat to IT network infrastructures. A lost or stolen computer, laptop, or device is one of the most common causes of a HIPAA data breach. As a result, medical practices are advised to abide by the following physical security requirements:
1. Facility access control
Implement measures to control physical access to areas where PHI is stored, processed, or transmitted. This includes locks, access cards, and security badges.
2. Workstation and device security
Secure workstations and mobile devices (e.g., laptops, tablets, smartphones) to prevent unauthorized access to PHI. This may involve encryption, password protection, and physical security measures or a combination thereof.
3. Device and media control
Safeguard removable media (e.g., USB drives, CDs) and their use to prevent the unauthorized access or disclosure of PHI.
Technical safeguards
HIPAA regulations extend beyond paperwork, encompassing technical and IT requirements as well. For many administrators, navigating these technical aspects can be daunting as their constant evolution can make it challenging to stay current on the latest cyber threats to the facility’s systems. These technical safeguards include:
1. Access control
Implementation of access controls, such as user authentication and role-based access, to ensure that only authorized individuals can access electronic PHI.
2. Audit controls
Implementation of hardware, software, and procedural mechanisms for recording and examining system activity related to ePHI, including tracking logins, access, and modifications to ePHI.
3. Integrity controls
Ensuring the integrity of ePHI by implementing mechanisms to protect against unauthorized alterations or corruption of data during transmission or storage.
4. Transmission security
Encrypting ePHI during transmission over networks to protect it from interception by unauthorized parties.
5. Authentication
Implementing mechanisms to verify the identity of users and entities that access ePHI.
6. Encryption
Using encryption technologies to safeguard ePHI stored on electronic devices or transmitted over networks.
Aligning HIPAA to NIST CSF
As an industry, healthcare experiences the most cyberattacks, and the remediation costs are nearly double other industries. Cyber insurance policies have also skyrocketed in recent years, and insurers are increasingly demanding certain certifications and/or technologies before issuing policies.
To bring a more standardized approach to cybersecurity, hospitals are aligning their cyber strategies to the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF).
Nearly a decade ago, NIST CSF was released as a crosswalk between the broad HIPAA goals on administrative, physical, and technical safeguards to help organizations identify gaps and increase compliance.
According to the NIST framework, “If a covered entity has an existing security program aligned to the HIPAA Security Rule, the entity can use this mapping document to identify which pieces of the NIST Cybersecurity Framework it is already meeting and which represent new practices to incorporate into its risk management program.”
Working with the OCR, NIST is in the process of updating guidance on how to comply with the HIPAA Security Rule.
Security is not compliance. Compliance is not security.
Security and compliance are not synonymous. While hospitals and entities that handle PHI must follow HIPAA cybersecurity requirements, compliance with those standards does not ensure even a basic level of security. At the same time, organizations that have a vigorous cybersecurity program may not be HIPAA-compliant.
That’s why a framework like NIST CSF is beneficial. It can bring security and adherence to regulations, aiding hospitals and health systems by providing a blanket of protection over their cybersecurity assets while maintaining compliance.
To gain more insights and practical knowledge that can help safeguard your healthcare organization in the face of evolving cyber challenges, check out our on-demand webinar, “A New Era of Cybersecurity.”

